Michael Manley 9/1/2017 “Use Security Software to protect your Computer and your Business Computer”
If you’ve been reading the steady supply of “bad news” articles that bombard us about hackers, identity theft, invasions of privacy, leaked photos, lost data and productivity, security breaches etc, you are probably ready to burn your computer and begin hunting for typewriters and encyclopedias at the local thrift store. Not to fear – there are some easy steps anyone can take to decrease their online risks. Consider these ways to boost your computer’s “immune system”.
Use Security Software (Antivirus)
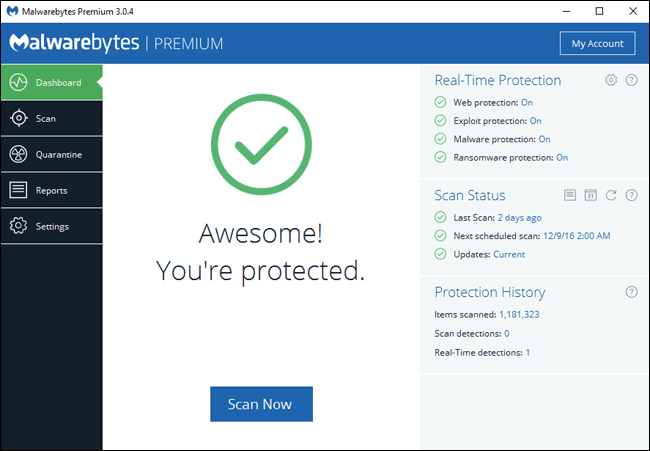
First things first. Every few years someone will claim that antivirus software is no longer relevant. Unless you happen to be a security expert and also an expert programmer/hacker in your spare time (or live a really unique lifestyle that will not apply to any of our clients reading this) you need antivirus. It’s cheap insurance against the proliferation of ever evolving online threats. Not only do you need antivirus, but you should invest in a paid subscription with one of the leading security software providers. Yes, you can find free antivirus software, but there is a reason so many industry professionals recommend premium paid software. No solution is 100% “bullet-proof”, but remember the old adage, “you get what you pay for”. New threats arrive every day, and the good companies must analyze and respond to the threats as they are detected.
Another urban rumor – I still occasionally meet Apple fanatics who believe Macs are immune to viruses. I hate to break it to you, but Macs get viruses too. The more popular they become as personal computers, the more they are targeted by cyber criminals and the more susceptible to viruses they become.
So do you really want to risk the lost productivity (downtime) and repair costs involved with getting a virus to save $40/year or prove that you are some “cyber stud” who’s immune to security threats? Our average client spends about $150 in repairs (parts and software) to get up and running again after an infection. That does not include the system downtime which can add up to thousands more dollars to a business in lost productivity/revenue.
Just because your computer came with or had antivirus software on it at one point, doesn’t mean your subscription is still active. One of the most common issues we find when new customers call is about virus issues is that they ignored or missed the notifications to renew their antivirus software, and have been unprotected for years in many cases. Make sure you check your antivirus status monthly, or let an IT professional (like Odyssey) monitor it for you.
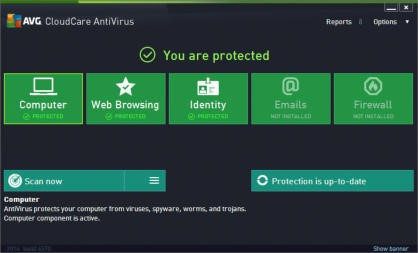
Sometimes, in addition to antivirus, we also recommend using Malwarebytes with your paid antivirus. Malwarebytes can provide extra protection against malicious software that traditional antivirus products may not. Browser hijackers, Spyware, Adware, Data mining, etc. are just a few unwanted software programs that are technically not viruses. Trust us though, life is better without them and Malwarebytes has free and paid versions available to remove those undesirable “residents” from your computer.

Get Protected Today
Existing Odyssey Customers.
Continue Existing Service Ticket
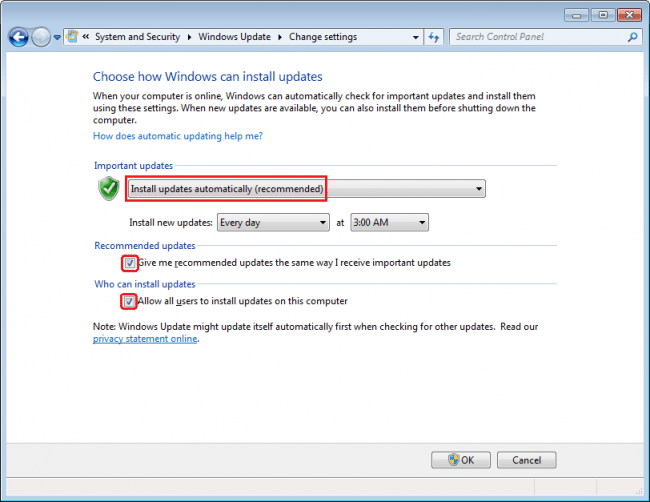
Are you getting Automatic Updates?
Almost all the software on your computer has security issues – especially your most used programs. We’re talking about the Windows operating system, Google Chrome, Java, Mozilla Firefox, Adobe Flash, Adobe Reader, Microsoft Office—the list goes on. The companies that produce this software release regular updates to fix vulnerabilities and problems that have been identified, but in many cases, you may not be getting them.
Many programs now come with automatic updates so it can update itself in the background without any input from you.
Many of our clients enable/disable these updates, often without even realizing it. While the Windows restarts after installing an update are annoying, running vulnerable software is far worse in the long run.
Be sure to check if your updates and security patches are running on a regular basis. Sometimes these updates will have unintended negative consequences or errors installing. In those cases, you will need to contact an IT professional (like Odyssey). Monitoring and resolving these conflicts and ensuring the updates apply successfully is a feature we offer in our Managed Services packages.
Better Passwords and How to Manage Them
Now we need to talk about those annoying things you are constantly being prompted for – yes we are talking about passwords. Believe it or not, those login screens are actually there to protect you. Maybe a programmer is laughing in his cubicle somewhere, but the reality is that strong passwords can literally “save your bacon”.
I’m sure none of you use the same password for everything 😉 Especially the password that’s been on that yellow sticky note attached to your monitor for the last 10 years? Reality Check –People get hacked all the time, and using the same password everywhere just makes all your accounts vulnerable to cyber predators.
Because using separate complex passwords for each site/service can be a daunting if not impossible task, we recommend using a password manager like LastPass. It can automatically generate the passwords for you while saving them in a secure place to save your brain cells as you browse and do your daily tasks.
https://www.tomsguide.com/us/best-password-managers,review-3785.html

As my grandfather always said, “locks keep honest people honest”. The idea of using passwords is to deter cyber criminals. Do your due diligence and they will likely leave you alone and look for easier prey.
Consistent verified offsite backups (that are encrypted) can sometimes be the best route to recovery. Pricing has really become affordable for both business and residential customers with customized solutions based on your unique needs. Learn More Here.
It’s worth noting here that encryption can be used to further protect your data. There are ways to bypass passwords, especially if someone has physically stolen your device. In those cases, encryption may be the only barrier left to protect your personal information. Contact your IT professional (like Odyssey) to learn more about encryption and what solution works best for your unique situation.

Other Computer Security Tips:
Back to the discussion on passwords and security breaches – never let your phone or computer out of your sight in public. Leaving it sitting on the dash of your car at the gas station or on the table while you use the restroom at a restaurant is all it takes.
Stolen devices will hurt your wallet, but sometimes they can also cause damage to your reputation, career, family, friendships, etc, especially when you haven’t implemented the steps above.
Don’t fall for Scams and Phishing attempts

Don’t open emails from strangers, and don’t click on links in emails that look suspicious. Remember, often they can appear legitimate, but are actually fake. These attempts are known as phishing.
Ideally, you would avoid all email links, but that’s not realistic in our fast-paced information rich social culture. Instead, you may opt to check the link before you commit by clicking on them.
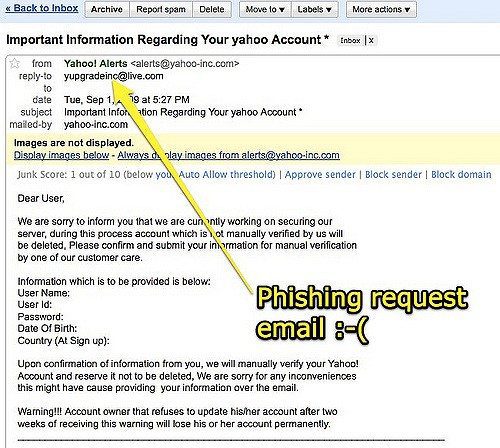
If the link says “amazon.com”, but the real destination says “amazon.clickme.com”, stop and don’t go any further because something is suspicious. Remember, just because it has a word you recognize like “Amazon” it doesn’t mean it’s actually going to Amazon.
Microsoft does not call you about your computers, and the FBI does not send a message to your computer.
Far too many innocent people have been robbed of their hard earned dollars by pop-ups that appear legitimate but are actually attempts to steal your hard-earned cash. Develop a relationship with a reputable IT professional (like Odyssey) and use them to help you when you have tech support issues rather than faceless companies from a distant country. Professionals can diagnose your problem and advise proper actions (like removing the malicious software that is telling you that you have a problem in the 1st place).
Don’t Trust Your Popup Notifications
Watch for attempts by obscure websites to get you to install seemingly legitimate updates. Cyber criminals use these methods to get you to allow programs that can ultimately allow them to compromise your computer. If you do suspect you have plug-ins or applications that need updating, close the popup and go to the developer’s website instead.
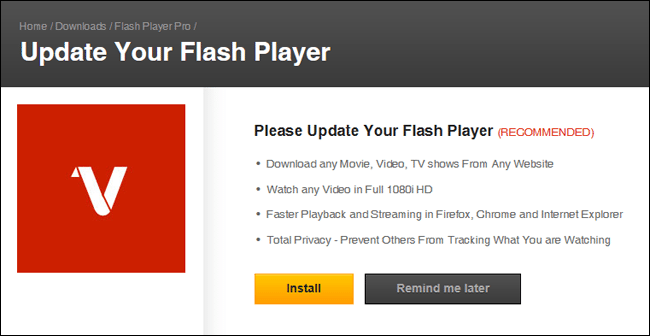
Avoid the Junk – Don’t install extra “free” software
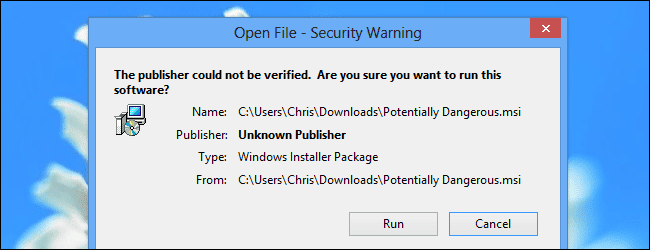
Many slow computers that come to our office are running programs the owner does not recognize or even remember installing. We see so windows that pop up and ask our permission to run that few of us take the time to actually read what we’re installing anymore. Then one day you realize it takes your computer 5 times longer to do the tasks you used to do and you’ll find yourself in our office asking to have it cleaned-up and optimized.
Pay attention to the programs you download and run. Don’t let family members and friends install the latest free program on your computer to make your life better. Always ready the “fine print” before granting permission to applications. If in doubt, do not click “allow” or give it permission to install.
When you are intentionally installing new software, be sure to get it from its official website.—if you want to download Open Office, download it from Open Office’s official website. Don’t click a “Download Open Office” banner on another website and download a bundle from someone with unwanted malware or adware along with it. Carefully read to uncheck any bundled software that comes with a program—even a legitimate one.
Also, be sure to watch out for advertisement banners disguised as “Download” links that will take you elsewhere and try to trick you into downloading possibly malicious software.